Introducing a Comprehensive Python Vulnerability Taxonomy
Welcome to our community page dedicated to presenting and discussing our latest research on Python vulnerability classification. Our goal is to provide a detailed and systematic approach to understanding and categorizing Python vulnerabilities, fostering collaboration and continuous improvement.
Background and Motivation
In the ever-evolving field of software security, identifying and categorizing vulnerabilities is crucial for developing effective mitigation strategies. Our research builds upon established taxonomies such as Orthogonal Defect Classification (ODC) and Code Defects Classification (CDC), tailored specifically to address the intricacies of Python vulnerabilities.
Taxonomy Overview
Our taxonomy for Python vulnerabilities is designed to provide a comprehensive and detailed classification system, facilitating better understanding, detection, and mitigation of security issues. The taxonomy consists of 10 overarching categories and 41 subcategories, ensuring a nuanced and granular classification of each vulnerability.
Main Categories
- Input Validation and Sanitization: Issues related to improper validation or sanitization of user inputs.
- Authentication, Authorization, and Session Management: Vulnerabilities affecting authentication mechanisms, user authorization processes, and session management.
- Cryptographic: Issues related to cryptographic operations, including encryption, decryption, and key management.
- Design Defects: Flaws originating from poor software design decisions.
- Configuration Issues: Problems arising from improper software configuration.
- Memory Corruption: Vulnerabilities that lead to memory corruption, such as buffer overflows.
- Information Leakage: Issues that result in unintended exposure of sensitive information.
- Race Condition: Vulnerabilities caused by race conditions in software execution.
- Resource Management: Issues related to improper management of system resources.
- Numeric Errors: Vulnerabilities arising from improper handling of numeric operations.
Subcategories Example
Each main category is further divided into specific subcategories. For example, within the Cryptographic category, we have subcategories such as:
- Improper SSL/TLS Certificate Validation
- Weak Encryption Algorithm
Injection of arbitrary commands into user input. Improper sanitization of SQL queries leading to injection attacks. Unauthorized access to objects by manipulating references. Improper validation of file paths allowing unauthorized access to directories. Security issues during deserialization or parsing of data. Use of weak or easily guessable passwords. Flaws in the authentication process. Vulnerabilities related to session handling and management. Unauthorized elevation of user privileges. Plain-text communication allows sniffing of sensitive data. Weak encryption of sensitive data. Generation of inadequate random numbers. Improper validation of SSL/TLS Certificates. Vulnerabilities related to mistakes or flaws in cryptographic algorithms, methods, or libraries. Insufficient handling of unexpected errors or exceptions, potentially exposing sensitive information or causing system instability. Outdated and deprecated components that introduce a known vulnerability. Flaws in how the system manages user privileges and permissions, leading to unauthorized access. Insecure configuration leading to vulnerabilities. Injecting malicious code into web apps to compromise user data or actions. Unauthorized execution of actions through forged requests. Inclusion of remote files in web applications. Inclusion of local files in web applications. Improper handling of redirection URLs. Tricking the server to make unauthorized requests. Improper handling of dynamic libraries, potentially allowing malicious DLLs to be loaded and executed. Occurs when a program writes more data to a buffer than it can hold, potentially overwriting adjacent memory. Involves accessing memory locations outside the allocated boundaries, often leading to unintended consequences. Refers to using memory after it has been deallocated, potentially causing unpredictable behavior or vulnerabilities. Accidental exposure of sensitive information related to a system. Mishandling and exposure of sensitive information related to a user. Situations where the state of a resource changes between the time it is checked and the time it is used, leading to unexpected behavior. Occur when multiple threads or processes concurrently access and modify shared data, potentially resulting in unpredictable outcomes. Race conditions that specifically affect file operations, which may result in security vulnerabilities when handling files. Failure to release file handles after use, potentially leading to resource exhaustion or security vulnerabilities. Neglecting to close network socket handles, which can result in resource depletion or potential security issues. Failing to deallocate memory properly, causing the program to consume excessive memory resources. Depleting system resources, such as CPU, memory, or network connec- tions, due to poor resource management, potentially leading to system instability or denial of service. Occur when integer variables exceed their maximum values, often leading to unexpected or insecure behavior. Result from imprecise rounding of numerical values, potentially causing discrepancies in calculations. Stem from the finite precision of floating-point numbers, potentially causing inaccuracies in mathematical operations. Involve mistakes in numerical calculations, which can lead to unintended results or vulnerabilities in software. Our methodology for developing this taxonomy involved the following steps: Fig. 1 – Methodology overview We invite the community to contribute to our project by reviewing the classifications and suggesting modifications. Your contributions will help enhance the accuracy of our taxonomy and keep it up to date with the latest security trends. Our comprehensive Python vulnerability taxonomy aims to be a step towards better understanding and mitigating security issues in Python software. By collaborating with the community, we aim to continuously refine and improve this taxonomy, ensuring it remains relevant and accurate. We encourage you to explore our research, review the taxonomy, and contribute to the ongoing effort to enhance Python security. Thank you! _Naghmeh IvakiView full list of categories and subcategories
Input Validation and Sanitization
Command Injection
SQL Injection
Insecure Direct Object References (IDOR)
Path Traversal
Insecure Parsing or Deserialization
Authentication, Authorization, and Session Management
Weak Password Policy
Insecure Authentication Mechanisms
Session Management Issues
Privilege Escalation
Cryptographic
Unencryped communication
Weak Encryption Algorithm
Inadequate random number generation
Improper SSL/TLS Certificate Validation
Cryptographic Implementation Error
Design Defects
Inadequate Error Handling
Vulnerable and Outdated Componentes
Poorly Designed Access Controls
Security Misconfigurations (PROPOSED TO BE MOVED TO “CONFIGURATION ISSUES”)
Configuration Issues
Cross-Site Scripting (XSS)
Cross-Site Request Forgery (CSRF)
Remote File Inclusion (RFI)
Local File Inclusion (LFI)
Open Redirects
Server-Side Request Forgery (SSRF)
Dynamic Link Library (DLL) Loading Issues
Memory Corruption
Buffer Overflows
Out-of-Bound Accesses
Use-After-Free
Information Leakage
Information Disclosure
Insecure Handling of Sensitive Data
Race Condition
Time-of-Check to Time-of-Use (TOCTOU)
Data Race Conditions in Threads
Race Condition in File Operations
Resource Management
File Handle Leaks
Socket Handle Leaks
Memory Leaks
Resource Exhaustion
Numeric Errors
Integer Overflow
Rounding Errors
Floating-Point Precision Issues
Arithmetic Errors
Methodology
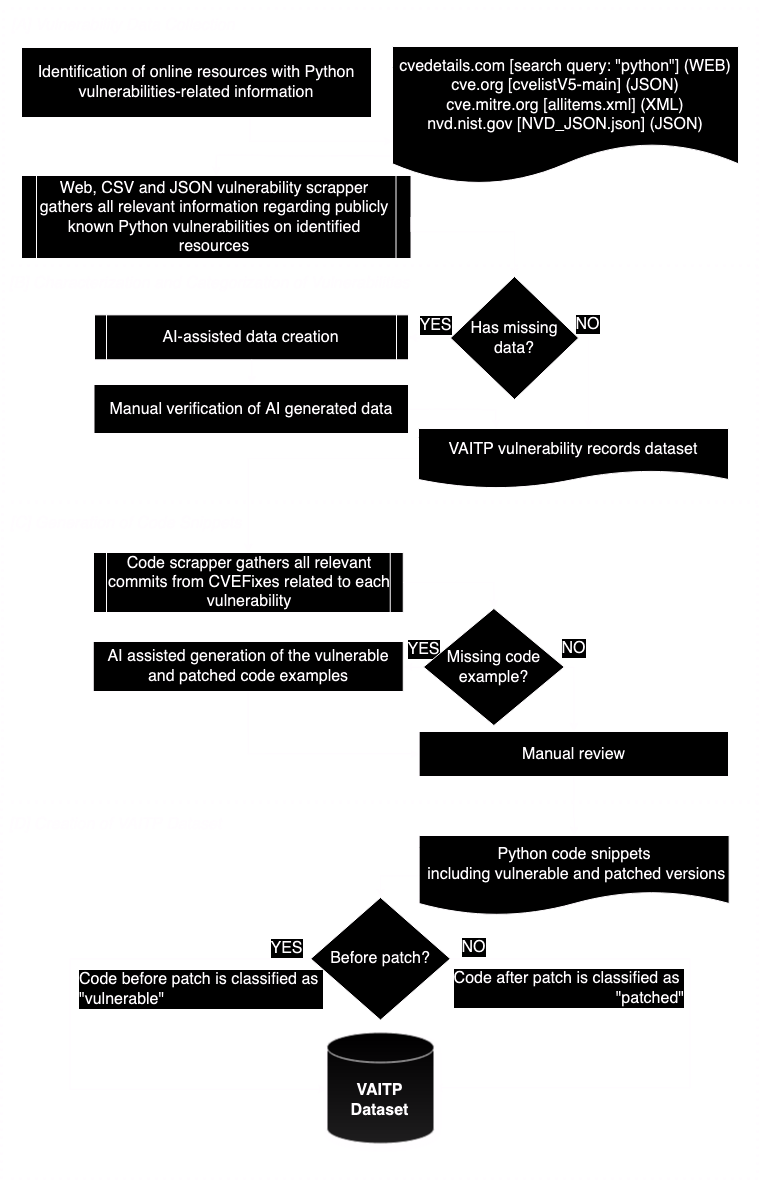
Community Involvement
How to Contribute
0xe8D4856d625C7aDBc8017c05C29d28E60145Bcc9Final notes
_Frédéric Bogaerts
_José Fonseca
